Dec 11, 2025
How Behavioral Monitoring Detects Marketing Threats

Averi Academy
Averi Team
8 minutes
In This Article
How behavioral monitoring tracks marketing activity, spots anomalies like account takeovers and insider data theft, and automates alerts across platforms.
Updated:
Dec 11, 2025
Don’t Feed the Algorithm
The algorithm never sleeps, but you don’t have to feed it — Join our weekly newsletter for real insights on AI, human creativity & marketing execution.
Behavioral monitoring helps protect your marketing systems by identifying unusual activities, such as suspicious logins, data exports, or workflow changes, in real time. It tracks user behaviors across platforms, compares them to normal patterns, and flags anomalies that may indicate security risks like account takeovers, insider threats, or API vulnerabilities.
Key Takeaways:
What It Does: Tracks user activity (e.g., logins, file access, API calls) to spot irregularities.
Common Threats Addressed: Account takeovers, insider data misuse, and API issues.
How It Works: Establishes a baseline for normal behavior and flags deviations.
Tools Involved: Integrates with CRMs, advertising platforms, and AI marketing systems like Averi AI.
Setup Steps:
Centralize activity logs.
Define normal patterns using historical data.
Automate alerts for deviations.
By combining AI-driven tools with human oversight, you can secure customer data, campaigns, and brand assets while minimizing disruptions.
Behavioral Threats - Suspicious User Activity Detection
Marketing Threats That Behavioral Monitoring Catches
Behavioral monitoring works by establishing a baseline of normal activity, allowing it to quickly identify unusual patterns and tighten security when deviations occur. Below are some common scenarios where detecting abnormal behavior can help prevent breaches.
Account Takeovers and Unauthorized Logins
Unusual login activity is one of the first red flags behavioral monitoring can catch. The system continuously tracks factors like login location, device type, and access timing. For instance, imagine a marketing manager who typically logs in from Chicago between 8:00 AM and 6:00 PM CST. If their account suddenly logs in from Romania at 2:00 AM, the system immediately flags this as suspicious. Similarly, a login from an unfamiliar device without multi-factor authentication or a series of failed login attempts followed by a successful one would trigger alerts. Another telltale sign is an "impossible travel" scenario - such as an account being accessed from New York at 10:00 AM EST and then from another far-off location just minutes later. These situations often prompt additional verification steps to secure the account.
Insider Threats and Data Theft
Behavioral monitoring doesn’t just guard against external threats; it also keeps an eye on insider activity. For example, if an employee who generally reviews 10–15 customer records per day suddenly exports a much larger number from the CRM, this could signal potential data theft. Similarly, unusual file-sharing behavior - such as forwarding sensitive information to a personal email or uploading it to unauthorized cloud storage - raises red flags. Such actions trigger alerts and are escalated for further investigation.
How to Set Up Behavioral Monitoring
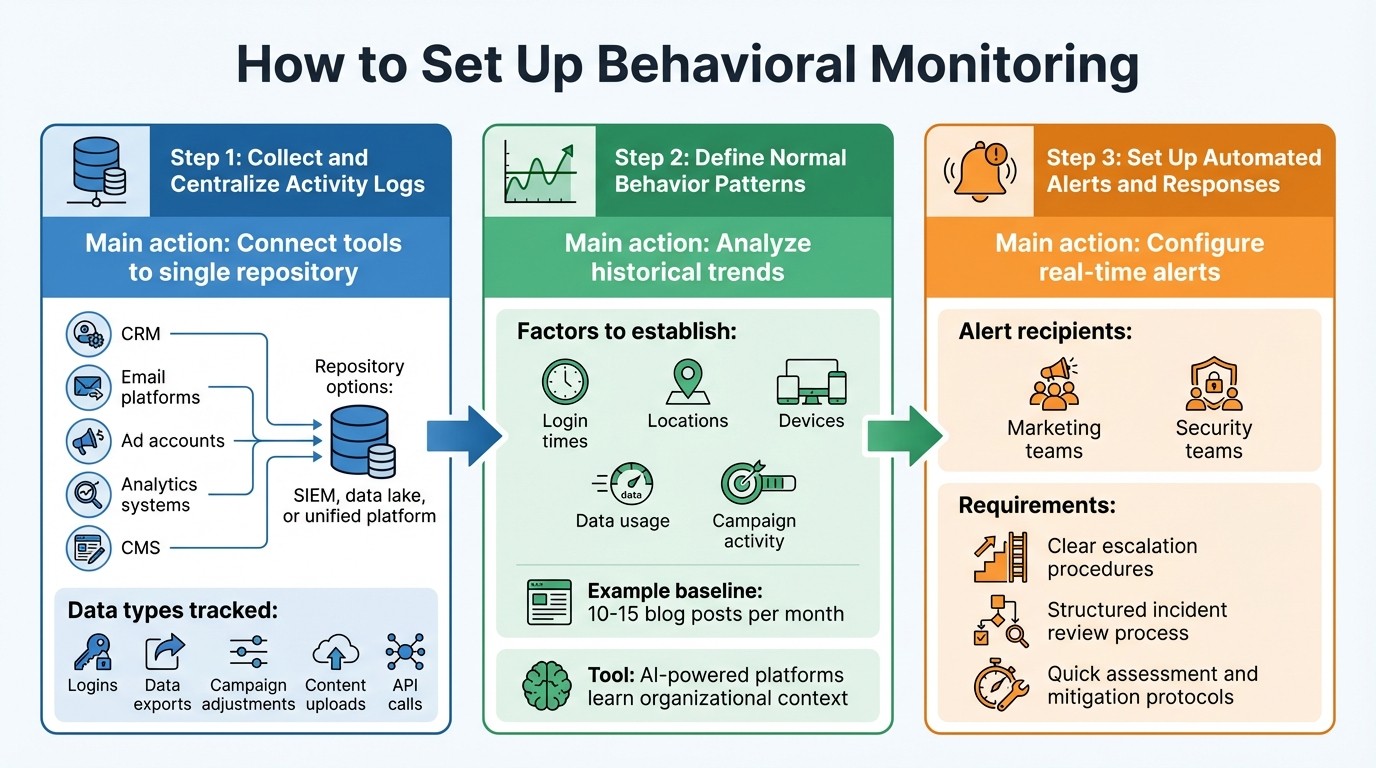
3-Step Behavioral Monitoring Setup Process for Marketing Security
Establishing behavioral monitoring involves three key steps: gathering data, defining typical behavior, and implementing alerts. Collaboration between marketing and security teams is essential to make this process effective.
Step 1: Collect and Centralize Activity Logs
Begin by connecting tools like your CRM, email platforms, ad accounts, analytics systems, and CMS to a single repository, such as a SIEM, data lake, or another unified platform. This ensures all activity data - such as logins, data exports, campaign adjustments, content uploads, and API calls - is consolidated. Without this centralization, it’s easy to miss threats that span multiple platforms or involve coordinated suspicious actions.
Step 2: Define Normal Behavior Patterns
With your data centralized, analyze historical trends to establish what "normal" looks like for your business. This includes factors like login times, locations, devices, data usage, and campaign activity. AI-powered marketing platforms can help by learning your organization’s unique context, including workflows, brand guidelines, and integrated data from tools like revenue and advertising systems [1]. These platforms can encode these patterns into workflows that flag anomalies. For instance, if your team typically publishes 10–15 blog posts per month and suddenly schedules a significantly higher number, the system can identify this as unusual and signal the need for review.
Step 3: Set Up Automated Alerts and Responses
Configure real-time alerts to notify you of any deviations from your established baselines. Ensure these alerts are routed to both marketing and security teams, along with clear escalation procedures. For significant anomalies, have a structured incident review process in place to quickly assess and mitigate potential threats.
Behavioral Monitoring in AI Marketing Platforms
AI marketing platforms bring workflows, assets, and team activities under one roof, making it easier to monitor behavior. This centralized approach lays the groundwork for advanced AI-driven security features, as highlighted below.
Using Averi AI for Security Monitoring
Averi AI's workspace design simplifies behavioral monitoring by centralizing activity tracking. With its AI-Enabled Asset Management system, assets are neatly organized into folders, allowing the platform to monitor access, modifications, and sharing patterns. Any unusual activity, like unexpected large downloads or irregular sharing of files, stands out against established norms. Additionally, Averi's Synapse architecture seamlessly integrates strategic discussions, content creation, and expert collaboration, creating a detailed log of marketing operations.
This monitoring goes beyond just asset management, extending to real-time tracking of marketing workflows for a more comprehensive security framework.
Spotting Unusual Activity in Marketing Workflows
Through its Create & Collaborate features, Averi AI keeps tabs on project involvement, content updates, and draft sharing. Irregularities - such as unauthorized changes to campaign materials, unexpected participation in sensitive projects, or abnormal sharing of drafts with external recipients - are flagged using its extensive activity tracking system [1]. Designed to think and operate like a marketer, Averi AI has a deep understanding of typical marketing workflows. This contextual awareness allows teams to set clear expectations for normal behavior. If team actions suddenly veer away from these norms, the platform triggers a review, helping to identify whether the change is legitimate growth or a potential security threat. By aligning its insights with marketing operations, Averi makes it easier to distinguish between routine scaling and suspicious activity.
Best Practices for Running Behavioral Monitoring
Regular Updates and Maintenance
Marketing operations are always evolving, and keeping your behavioral monitoring systems up-to-date is key to staying effective. What you considered "normal" activity a few months ago might now generate unnecessary alerts if your team structure or strategy has shifted. For AI-driven platforms, this means regularly updating your Infobase with current company details, revising your Brand Voice as communication strategies change, and tweaking process codifications to align with new operational realities. These updates ensure the system can differentiate between legitimate changes and potential threats, reducing noise and improving accuracy.
Marketing and Security Team Coordination
While behavioral monitoring tools can flag unusual activity, the real value comes from strong collaboration between marketing and security teams. AI may handle the heavy lifting of routine monitoring and alerting, but human expertise is essential for interpreting whether flagged events represent genuine threats or just operational changes. Kevin from Fieldgrade highlights this balance:
The AI handles what it should, and my team handles what we do best. No confusion about roles, no redundant work. Just better marketing, faster.[1]
This teamwork ensures flagged activities are addressed efficiently, creating a seamless approach that strengthens both security and marketing outcomes.
Privacy and Compliance Requirements
Behavioral monitoring inherently involves tracking team activities, which makes privacy and compliance non-negotiable. Focus on monitoring actions rather than personal data to respect individual privacy. Ensure your data handling practices align with relevant legal and ethical standards. Clearly document your monitoring policies, communicate them transparently to your team, and conduct regular reviews to maintain both compliance and trust. By doing so, you create a system that balances operational needs with respect for privacy.
Conclusion
Behavioral monitoring offers a real-time safety net against threats that can derail campaigns, compromise sensitive data, or disrupt operations. By analyzing activity patterns and immediately flagging anything unusual, these systems can intercept account takeovers, insider threats, and API exploits before they cause significant harm. The shift from reactive to proactive security is crucial - understanding what "normal" looks like and acting swiftly when something deviates is the foundation of this approach.
A strong monitoring strategy blends advanced technology with human insight. Combining AI-driven monitoring tools with human oversight ensures alerts are properly evaluated, reducing the noise of false positives while quickly identifying genuine risks. This balance is essential for maintaining an effective and efficient security posture.
For teams aiming to streamline both their security measures and marketing operations, platforms like Averi AI present a unified solution. As an AI Marketing Workspace, Averi AI consolidates marketing activities while offering a comprehensive view of team activity. Training the platform on your Brand Core and asset management not only enhances operational efficiency but also strengthens security - all from a single, integrated workspace.
To stay ahead, centralize logs, establish clear patterns of normal activity, and automate alerts to respond to anomalies instantly. Ensure your system evolves alongside your operations, creating a proactive framework that safeguards your campaigns while supporting innovation and growth.
FAQs
How does behavioral monitoring identify suspicious activity in marketing systems?
Behavioral monitoring works by analyzing user actions in real time and comparing them to standard, established patterns of behavior. It flags any unusual activity, such as logging in at odd hours, performing actions too quickly or excessively, or straying from typical workflows. These anomalies are then flagged for further investigation, making it easier to spot and address potential threats swiftly.
This method provides ongoing analysis, ensuring marketing systems stay protected while allowing regular operations to continue uninterrupted.
How does behavioral monitoring improve threat detection in AI marketing platforms?
Integrating behavioral monitoring into AI-driven marketing platforms strengthens both security and performance by spotting unusual activity as it happens. This real-time detection is crucial for preventing fraud, protecting brand reputation, and tackling potential problems before they grow into larger issues.
By actively analyzing user behavior, these systems not only keep campaigns running efficiently but also help achieve improved outcomes while reducing potential risks.
How can marketing and security teams work together effectively with behavioral monitoring tools?
Marketing and security teams can work together seamlessly by using behavioral monitoring tools to exchange real-time insights, spot unusual activities, and tackle potential threats before they escalate. These tools allow security teams to monitor system behaviors while giving marketing teams the ability to respond swiftly to any suspicious actions, safeguarding both campaign effectiveness and sensitive information.
Pairing AI-driven analytics with human expertise empowers teams to address risks proactively, strengthen system defenses, and keep campaigns running smoothly without jeopardizing security.





